Search Results for: Sim Database
-
Web Hacking

Hardening Web Servers
Hardening Web Servers: Web servers are one of the favorite areas for attackers to exploit because of the reach they…
Read More » -
Mobile

Penetration Testing Mobile Devices Using Android
Penetration Testing Mobile Devices: So how do we pen test mobile devices? In many ways the process is similar to…
Read More » -
Security+

Phishing, Spear Phishing, and Vishing
Phishing, Spear Phishing, and Vishing: Phishing is a form of social engineering in which you ask someone for a piece…
Read More » -
SQL Injection

SQL INJECTION ATTACKS: Finding the Vulnerability
SQL Injection Attacks: Now that we have the basics of SQL injection down, let’s use our DVWA environment to try…
Read More » -
SQL Injection
The SQL Interpreter
SQL Interpreter: One of the main aspects of this vulnerability that you must understand is that it leverages an SQL…
Read More » -
Nmap

NMAP SCRIPTING ENGINE: FROM CATERPILLAR TO BUTTERFLY
THE NMAP SCRIPTING ENGINE: FROM CATERPILLAR TO BUTTERFLY: Make no mistake. Nmap is an awesome tool. It is mature, robust,…
Read More » -
Black Hat

GOOGLE DIRECTIVES: PRACTICING YOUR GOOLGE-FU
Luckily for us, Google provides “directives” that are easy to user and help us get the most out of every…
Read More » -
AJAX
The Web Developer Bootcamp
Miscellaneous Hi! Welcome to the Web Developer Bootcamp, the best path you need to study net development. There are lots…
Read More » -
Microsoft Windows
Knowing Operating Systems Microsoft Windows
Understanding Operating Systems: We all say more about operating systems when we discuss scanning and enumeration, but for now, we…
Read More » -
Black Hat
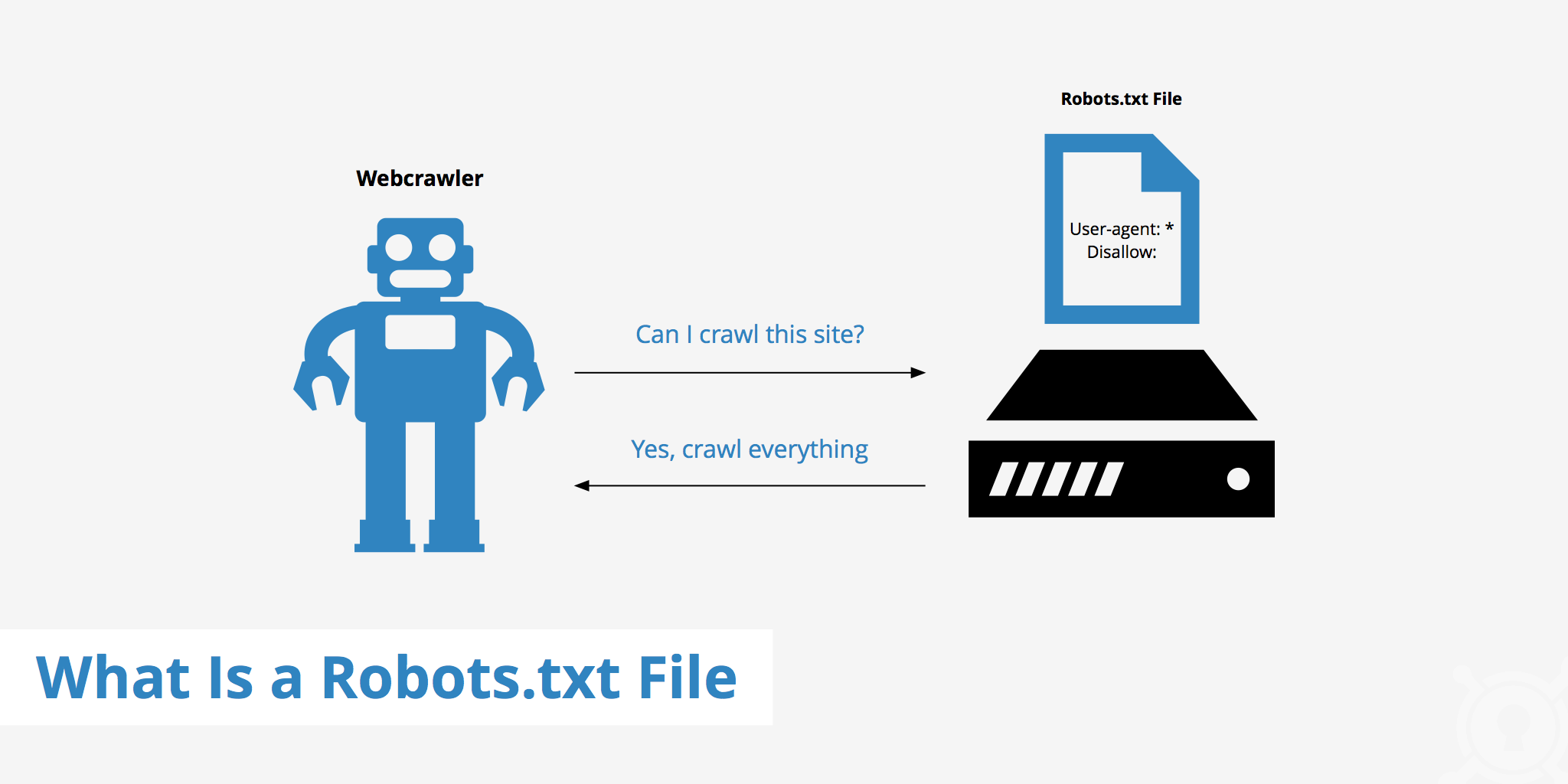
The Robots.txt File
The Robots.txt File One way to begin understanding what’s running on a web server is to view the server’s robots.txt…
Read More »