Proxies and Firewalls

Proxies and Firewalls: No network device discussion would be complete without delving into the world of proxies and firewalls. These devices are the bread and butter of ethical hackers in that they are the devices deliberately put in place to prevent unauthorized access. To test the strength of an organization’s perimeter is to ensure that its perimeter gate guard is alive and well.
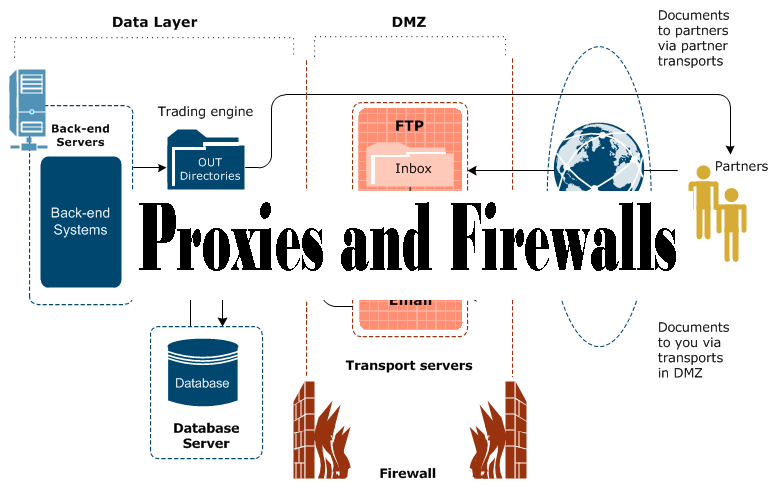
Proxies
Proxy servers work in the middle of the traffic scene. You may have been exposed to the forwarding side of proxies; for example, your browser at work may have been pointed to a proxy server to enable access to an outside resource such as a website. There are multiple reasons to implement such a solution. Protection of the internal client systems is one benefit.
Acting as an intermediary between the internal client systems and untrusted outside entities, the proxy is the only point of exposure to the outside world. It prevents the client system from communicating directly with the external source, thereby reducing exposure and risk. As the middleman, the proxy also has the capability of protecting users (client system) from themselves. In other words, proxies can filter traffic by content. This means proxies operate at the Application Layer (Layer 7).
A substantial leg up on lower-level firewalls, proxies can filter outgoing traffic requests and verify legitimate traffic at a detailed level. Thus, if users try to browse to, say, hackme.com, they will be denied the claim entirely if the filters are applied to prevent it. Proxies also speed up browsing by caching frequently visited sites and resources. Cached sites can be served to local clients at speed much faster than downloading the actual web resource.
NOTE: – The concept of proxy operation applies to other realms besides just caching traffic and being an Application layer firewall.
Firewalls
The firewall category includes proxy firewalls; however, because of a proxy’s varied functions, it seems appropriate to give them their subsection. Firewalls are most commonly broken down into the following main categories:
• Packet filtering
• Stateful packet filtering
• Application proxies, which we covered earlier
Packet-filtering firewalls look at the header information of the packets to determine legitimate traffic. Rules such as IP addresses and ports are used from the header to decide whether to allow or deny the packet entry. Stateful firewalls, on the other hand, determine the legitimacy of traffic based on the state of the connection from which the traffic originated.
For example, if a legitimate contact has been established between a client machine and a web server, if a logical connection has been established between a client machine and a web server, then the stateful firewall refers to its state table to verify that traffic originating from within that connection is vetted and legitimate.
NOTE: – Firewalls and Proxies are only as active as their configuration, and their arrangement is just as useful as the administrator creating them. Many firewall attacks are intended to circumvent them as opposed to a head-on assault; for us hackers, the softest target is our aim.
One Comment