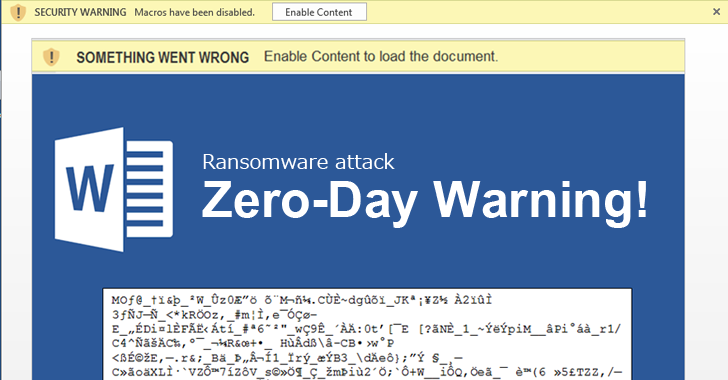
Microsoft Office Macros Still No. 1 Malware Delivery
Microsoft Office Macros Still No. 1 Malware Delivery: The Microsoft Office documents are responsible for the delivery of nearly half of all the malicious macros in August 2018, according to Confense.
A recent blog post found that macro remains the email attachment of choice for delivering malicious payloads. Around 45% of the attackers used these documents to delivery malicious macros, which include the Geodo, Chanitor, AZORult and GrandCrab.
According to the researchers, macro is one of the top choices because it either is enabled on a machine or only that requires a single mouse click to be enabled. “This makes it almost trivial to launch the very first stage of an infection chain,” Cofense wrote.
DO YOU KNOW? PhoneBook – Phone Search Database
Well, it is every time the same case that the Microsoft Office macro feature that is always enabled by default, which is why the users are unaware that there were any problems with opening the document. Yet the researcher who has noted that even with the appropriate protection in the place, users only have to see a warning that can be easily dismissed with just a single click.
“Abuse of this feature can be easily mitigated by disabling macros enterprise-wide. However, macros do have the legitimate and valuable usage, upon which many businesses rely. To help reduce the attacks surface introduced by this feature, businesses have some option,” Confense wrote.
Defending against the phishing attacks is far harder by the social engineering tactics. Additional findings from FireEye study, that revealed one in every one hundred emails that represents a phishing or malicious email. Of those email attacks over 90% of which are malware-less. The goal of malware-less attacks is to trick the users to share the information regarding the company by impersonating a trusted source.
“Phishing has been around since the mid-to-late ‘90s, and yet it’s still a significant problem as a direct effect of how successful it remains, even decades later. People are, and always will be, the weakest link,” said Thomas Pore, Director of the IT and services for Plixer.
“Social engineering will succeed, which means your organization is vulnerable. You must constantly monitor the network traffic and digital communication to look for behavior anomalies. Operating the SOC under the assumption that you have already been infected puts you in a state of mind to stay diligent when network traffic behavior anomalies rise up. A combination of regular staff training, critical-asset tagging, patching and behavior anomaly detection is the foundation of a strong and successful security program.”

![Bykea Had Publicly Exposed 400+ Million Users Data Including [CNIC, Address, License] ETC](https://www.techietalks.online/wp-content/uploads/2021/02/Bykea-Data-Breached.png)


2 Comments