Identifying Denial-of-Service and Distributed Denial-of-Service Attacks
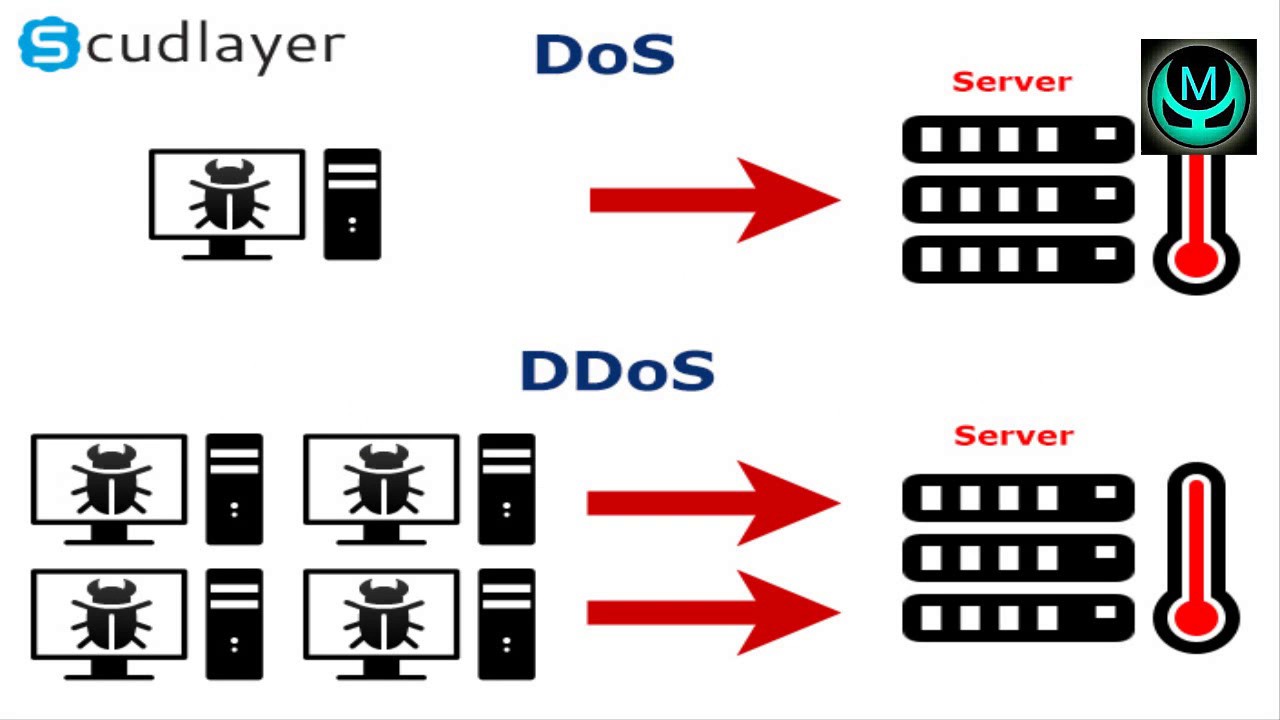
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks: Denial-of-service (DoS) attacks prevent access to resources by users authorized to use those resources.
An attacker may attempt to bring down an e-commerce website to prevent or deny usage by legitimate customers.
Most simple DoS attacks from a single system, and a specific server or organization is the target.
TIP: there is not a single type of DoS attack but a variety of similar methods that have the same purpose. It’s easiest to think of a DoS attack by imagining that your servers are so busy responding to false requests that they don’t have time to service legitimate requests. Not only can the servers be physically busy, but the same results can also occur if the attack consumes all of the available bandwidth.
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks
Several types of attacks can occur in this category. These attacks can do the following:
- Deny access to information, applications, systems, or communications.
- Bring down a website while the communications and systems continue to operate.
- Crash the operating system (a simple reboot may restore the server to normal operation).
- Fill eth communications channel of a network and prevent access by authorized users.
- Open as many TCP sessions as possible; this type of attack is called a TCP SYN flood DoS attack.
Two of the most common of DoS attacks are the ping of death and the buffer overflow.
The ping of death crashes a system by sending Internet Control Message Protocol (ICMP) packets (think echoes) that are larger than the system can handle.
Buffer overflow attacks, as the name implies to put more data (usually long input strings) into the buffer than it can hold. Code Red, Slapper, and Slammer are all attacks that took advantage of buffer overflows, and sPing is an example of a ping of death.
A distributed denial-of-service (DDoS) attack by using multiple computer systems (often through botnets) to conduct the attack against a single organization.
These attacks exploit the inherent weaknesses of dedicated networks such as DSL and cable. These permanently attached systems usually have little, if any, protection.
An attacker can load an attack program onto dozens or even hundreds of computer systems that use DSL or cable modems.
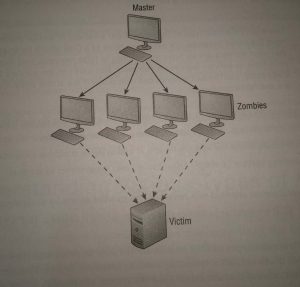
The attack program lies dormant on these computers until they get an attack signal from a master computer.
The signal triggers the system, which launch an attack simultaneously on the target network or system.
DDoS attacks are common on the internet, where they have hit large companies, and such attacks are often widely publicized in the media.
Below shows an attack is occurring and the master controller orchestrating the attack.
The master controller may be another unsuspecting user. The system talking direction from the master control computer is referred to as zombies or nodes.
These systems merely carry out the instruction they have been given by the master computer.
Distributed Denial-of-Service Attack
TIP: Remember that the difference between a DoS attack and a DDoS attack is that the latteruses multiple computers-all focused on one target. DDoS is far more common-and effective-today than DoS.
The nasty part of this type of attack is that the machines used to carry out the attack belong to normal computer users.
The attack gives no special warning to those users. When the attack is complete, the attack program may remove itself from the system to infect the unsuspecting user’s computer with a virus that destroys the hard drive, thereby wiping out the evidence.
Can You Prevent Denial Attacks?
In general, there is little you can do to prevent DoS or DDoS attacks. Many operating systems are particularly suspecting to these types of attacks.
Fortunately, most operating system manufactures have implemented updates to minimize their effects. Make sure your operating system and the applications you use are up-to-date.
If you have any question regarding identifying denial-of-service and distributed denial-of-service attacks click here to ask.

![Bykea Had Publicly Exposed 400+ Million Users Data Including [CNIC, Address, License] ETC](https://www.techietalks.online/wp-content/uploads/2021/02/Bykea-Data-Breached.png)


it is helpful i appriciate