Firewall Configuration in Network Security
Firewall Configuration: Not all firewalls or firewall setups are created equally, so you need to be familiar with each setup and how it works.
Firewalls can be set up and arranged in several ways, each offering its own advantages and disadvantages. In this section we will cover each method.
Bastion Host: A bastion host is intended to be the point through which traffic enters and exits the network.
It is a computer system that hosts nothing other than what it needs to perform its defined role, which is this case, is to protect resources from attack. This type of host has two interfaces: one connected to the public network and the other to the internal network.
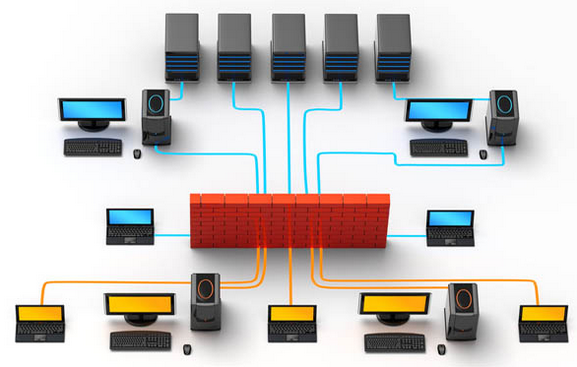
Screened Subnet: This type of setup uses a single firewall with three built-in interfaces. The three interfaces are connected to the Internet, the DMZ (more on this in a moment), and the intranet, respectively.
The obvious advantage of this setup is that the individual areas are separated from one another by virtue of the fact that each is connected to its own interface.
This offers the advantage of preventing a compromise in one area from affecting one of the other areas.
Multihomed Firewall: A multihomed firewall refers to two or more networks. Each interface is connected to its own network segment logically and physically.
A multihomed firewall is commonly used to increase efficiency and reliability of an IP network. In this case, more than three interfaces are present to allow for further subdividing the system based on the specific security objectives of the organization.
Demilitarized Zone: A DMZ is a buffer zone between the public and private networks in an organization. It is used to act as not only a buffer zone but also a way to host services that a company wishes to make publicly available without allowing direct access to their own internal network.
A DMZ is constructed through the use of a firewall. Three or more network interfaces are assigned specific roles such as internal trusted network, DMZ network, and external untrusted network (Internet).
NOTE: Remember that each implementation is a little different in how it functions you should know the cast of characters involved in its layouts.