Web Hacking
-
Noteworthy HTTP Headers
Noteworthy HTTP Headers: Each HTTP cycle also includes headers in both the client request and the server response that transmit…
Read More » -
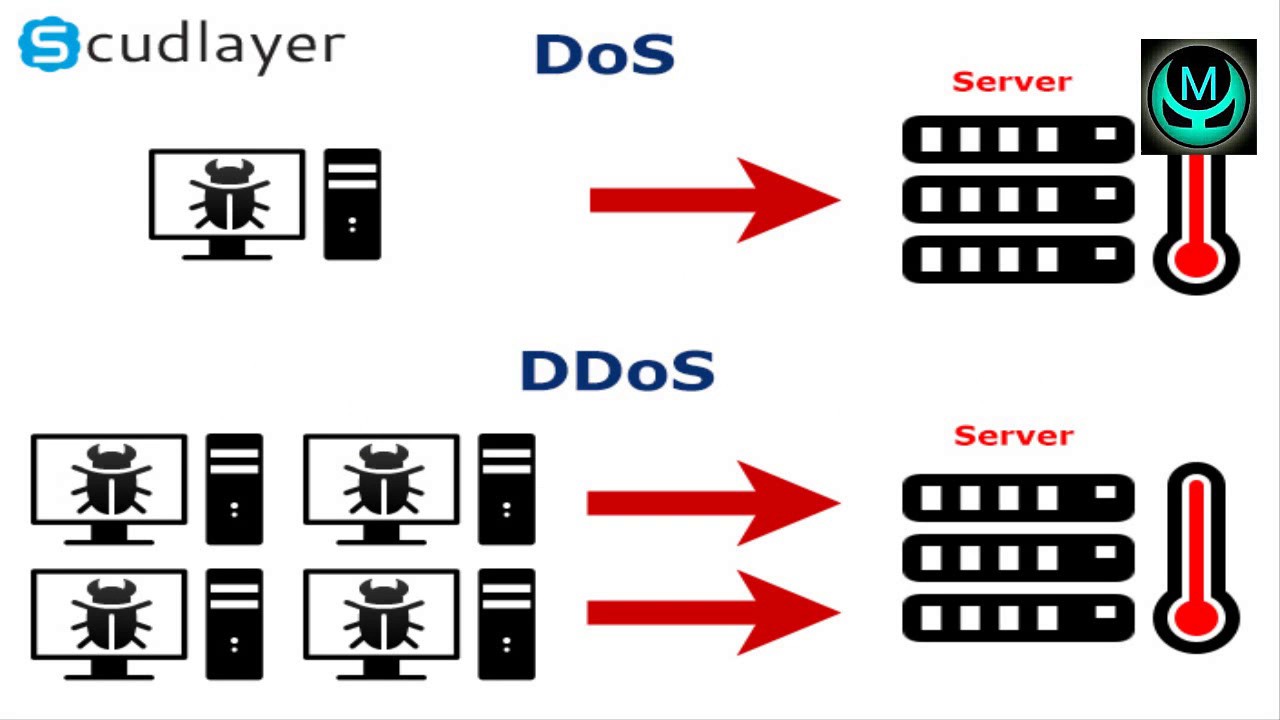
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks: Denial-of-service (DoS) attacks prevent access to resources by users authorized to use those resources.…
Read More » -
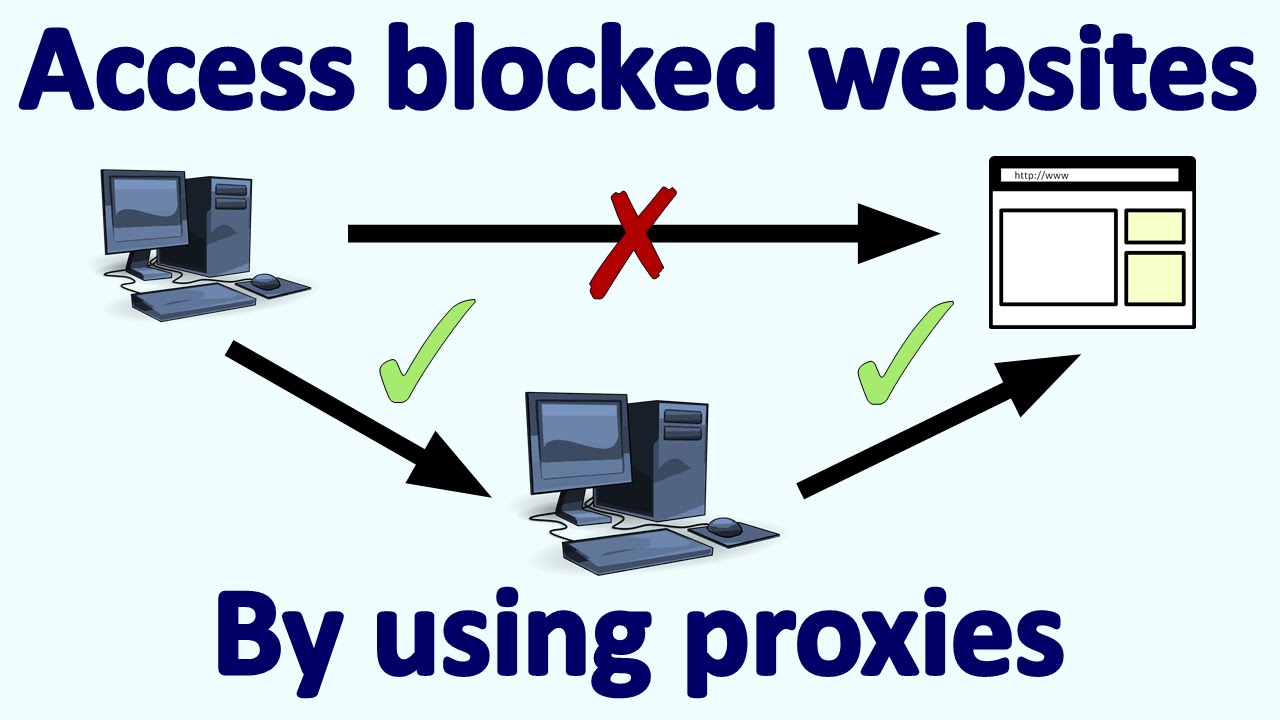
Setting a Web Browser to Use a Proxy | Using Proxies
Using Proxies A proxy is a system acting as a stand-in between the scanner and the target. The proxy acts…
Read More » -

Using Google Hacking
Using Search Engines One of the first step in the process of foot-printing tends to be using a search engine.…
Read More » -
Unrevealed Secret DOS Commands For Ethical Hackers
Unrevealed Secret DOS Commands For Ethical Hackers You will learn the DOS (Disk Operating System) best skills in this Course.…
Read More » -
DoS Tools Download And Run
DoS Tools The Follow is a list of DoS tools: DoSHTTP DoSHTTP is an HTTP flood DoS tool. It can…
Read More » -

Understanding DDoS And Botnets
Understanding DDoS Distributed denail-of-service (DDoS) Attacks have the same goals, but the implementation is much more complex and wields more…
Read More » -

The Open-Source Security Testing Methodology Manual (OSSTMM) & (PTES)
The Open-Source Security Testing Methodology Manual (OSSTMM) The OSSTM was created in a peer review proves that created cases that…
Read More » -

Download For Free Bug Bounty Web Hacking Course
Bug Bounty program is a special deal which is offered by many giant companies or websites & software developers by…
Read More » -
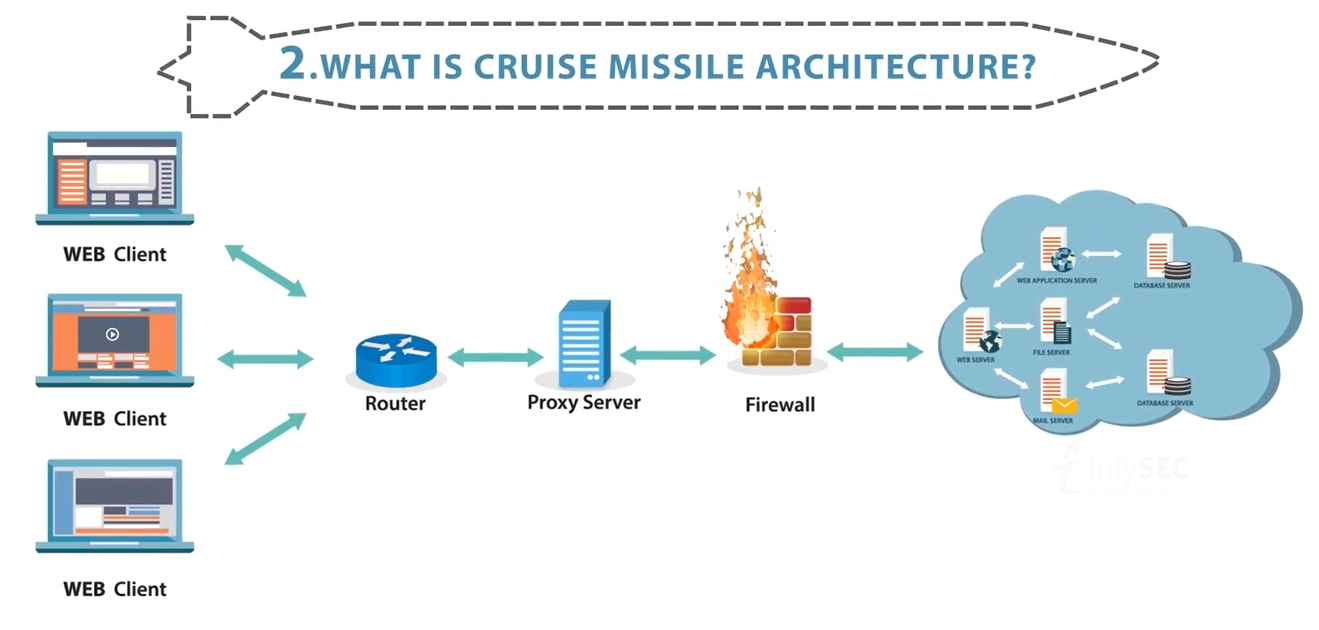
Download Web Hacking and Security Basic to Advance Level Course For Free
It’s one of the amazing course you ever seen and the best part is its all hands on practicle. In…
Read More »