Security+
-

Historically High Q2 for Mobile Banking Trojan
Historically High Q2 for Mobile Banking Trojan: Mobile banking Trojan is ranked as the top security problem in the second…
Read More » -

Dixons Carphone: Breach Hit 10 Million Personal Records
Dixons Carphone has revealed its estimation of how much the customer data was stolen in the recent disclosed breach by…
Read More » -

Types of Biometric Controls
There are a number of biometric controls that are used today; below we have the major implementations and their specific…
Read More » -

PERSONNEL SECURITY
Users can pose the biggest security risk to an organization. Background checks should be performed, contractors who needs to be…
Read More » -

YouTube Launches New Tool For Finding and Removing Unauthorized Re-Uploads
Re-uploading videos on YouTube is a favorite scammy channel that gets profit from other people’s hard work. The Copyright owners…
Read More » -
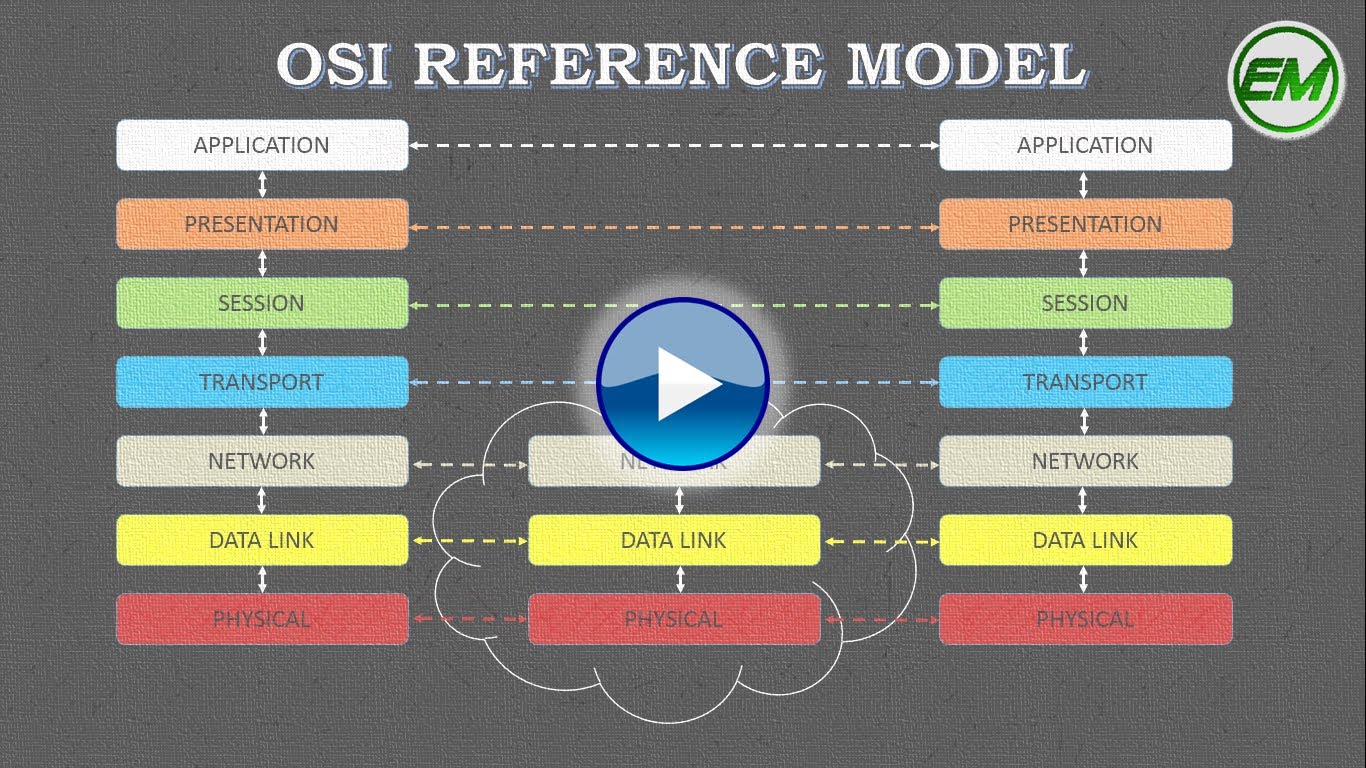
THE OSI MODEL
The OSI (Open System Interconnection) reference model is a layered network model. The model is of course abstract; we do…
Read More » -
SYSTEM VULNERABILITIES, THREATS, AND COUNTERMEASURES
System threats, vulnerabilities, and countermeasures describe security architecture and design vulnerabilities, as well as the corresponding exploits that may compromise…
Read More » -

Information Security Governance
Information security governance is the information security in the organizational level, which includes senior management, policies, processes, and staffing. It…
Read More » -

Legal and Regulatory Issues
Though general understanding of the major legal systems and their types of law is really essential, it is critical that…
Read More » -

Protocol Analyzers
The terms protocol analyzing and packet sniffing are interchangeable. They refer to the process of monitoring the data that is…
Read More »