Security+
-
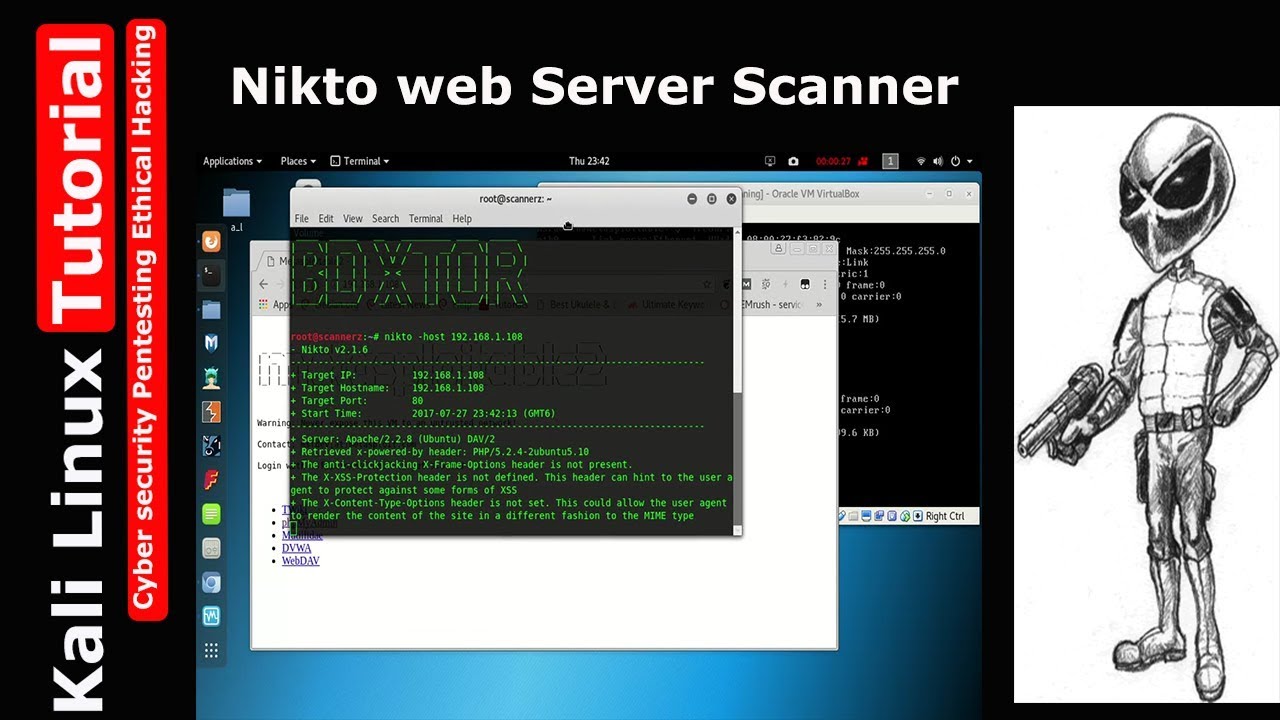
NIKTO: INTERROGATING WEB SERVERS
NIKTO: INTERROGATING WEB SERVERS: After running a port scan and discovering a service running on port 80 on port 443,…
Read More » -
USING NMAP TO PERFORM AN SYN SCAN
USING NMAP TO PERFORM AN SYN SCAN: The SYN Scan is arguably the most popular Nmap port scan. There are…
Read More » -

The Art of the Ethical Hack: A Q&A with Muhammad Taha Researcher at Riphah International University
1: How to start a career as an Ethical Hacker? To start a career as CEH, learn the fundamentals of…
Read More » -

Tracing the Evolution Cryptography
Tracing the Evolution: As with the ancient Egyptians and Romans, who used secret writing methods to obscure trade or battle…
Read More » -
Knowing Operating Systems Microsoft Windows
Understanding Operating Systems: We all say more about operating systems when we discuss scanning and enumeration, but for now, we…
Read More » -

Digital Millennium Copyright Act (DMCA)
Digital Millennium Copyright Act (DMCA): The DMCA is not often considered in a discussion of hacking and the question of…
Read More » -

Ethics and The Law
Ethics and The Law: As an ethical hacker, you need to be aware of the law and how it affects…
Read More » -
Understanding Hashing
Understanding Hashing Simply yet, hashing can be considered a type of one-way encryption. Most accurately, it is a process that…
Read More » -

Cyber Security Enhancement Act of 2002 – CSEA
Cyber Security Enhancement Act of 2002 – CSEA Several years ago, Congress determined that the legal system still allowed for…
Read More »
