Security+
-

Burp Suite
Burp Suite: For our purposes, we will use Burp Suite Intercept (or just Burp for short) as our proxy as…
Read More » -
BRUTE FORCE AUTHENTICATION ATTACKS
Brute Force Attacks: Authentication actually takes place in many other parts of the web application other then the main login…
Read More » -

SSL and TLS
SSL and TLS: Secure Sockets Layer (SSL) is used to establish a secure communication connection between two TCP-based machines. This…
Read More » -
Understanding Cryptography Standards and Protocols
Understanding Cryptography Standards and Protocols: Numerous standards are available to establish secure service. Some of the standard that will be…
Read More » -

Phishing, Spear Phishing, and Vishing
Phishing, Spear Phishing, and Vishing: Phishing is a form of social engineering in which you ask someone for a piece…
Read More » -

Spoofing Attacks – Understanding Various Types of Attacks
Spoofing Attacks: A spoofing attack is an attempt by someone or something to masquerade as someone else. This type of…
Read More » -
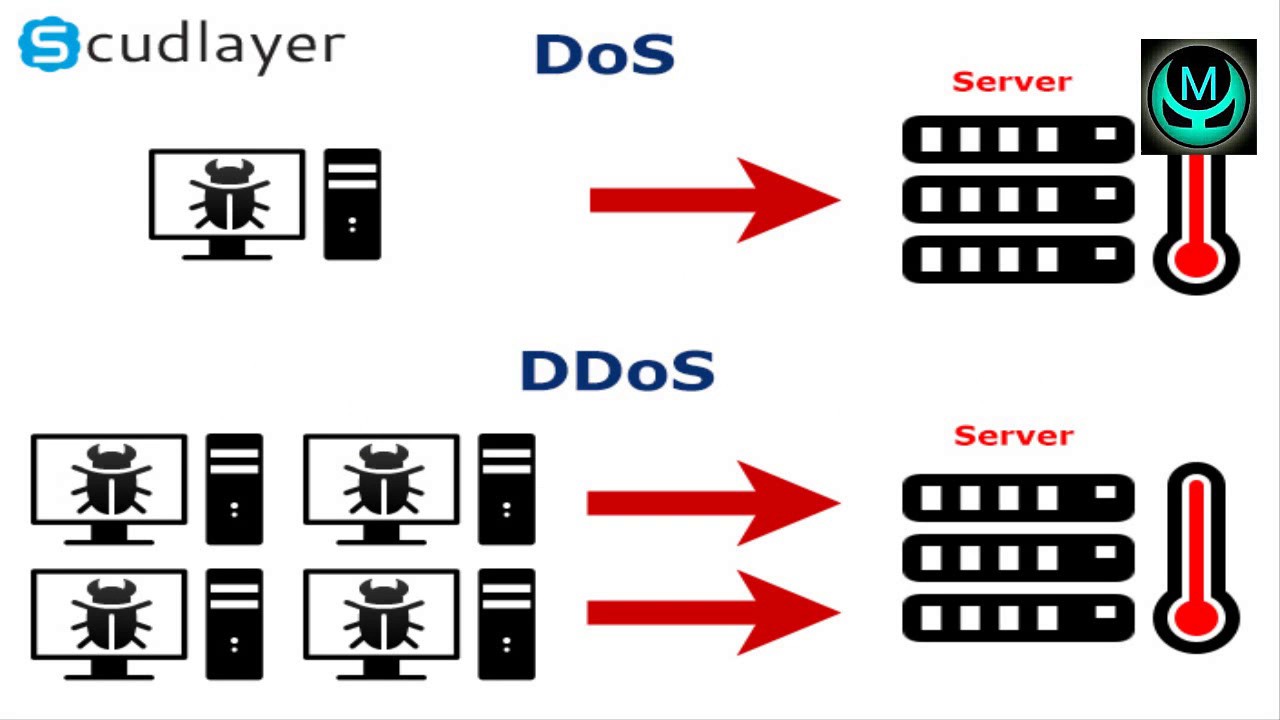
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks: Denial-of-service (DoS) attacks prevent access to resources by users authorized to use those resources.…
Read More » -
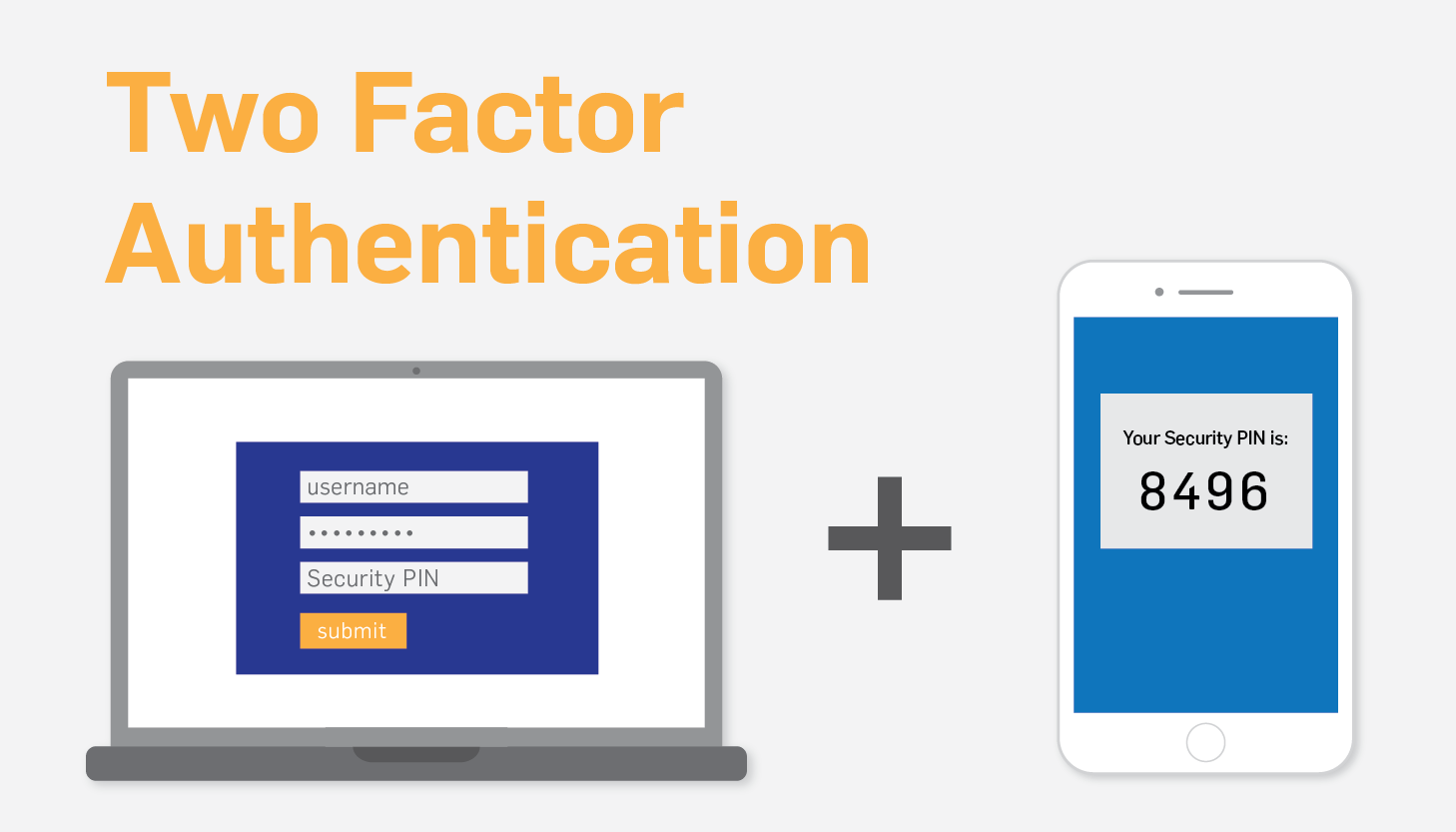
Authentication (Single Factor) and Authorization
Authentication (Single Factor) and Authorization: The most basic form of authentication is known as single-factor authentication (SFA), because only one…
Read More » -

VPNs and VPN Concentrators
VPNs and VPN Concentrators: A virtual private network (VPN) is a private network connection that occurs through a public networks.…
Read More »
