IT Security
-
Locating Database on the Network
A tool that is effective at locating rogue or unknown database installation in SQL Ping 3.0, as described on the…
Read More » -

Introducing SQL Injection, SQL Attacks in Action And Results of SQL Injection
Introducing SQL Injection, SQL Attacks in Action And Results of SQL Injection The acronym SQL(pronounced sequel) stands for Structured Query…
Read More » -
Creating Simple Virus Via Notepad And JPS Virus Maker
How to Create a Virus Creating a virus is a process that can be very complicated or something that happens…
Read More » -

Notes On Beginner Intermediate And Advanced Level Networking Docs/PDFs For Free
Beginner Intermediate And Advanced Level Networking Docs/PDFs For Free Notes on Networking For Beginners, Intermediate and Advanced Level students. You…
Read More » -
Gaining Network Information
Gaining Network Information Via Whois And Nslookup An important step in foot printing is to gain information, where possible, about…
Read More » -
How To Find Serial Key Of Any Software
Let’s Find Out The Serial Key of Any Software? The key 94FBR is a part of Office 2000 Pro CD…
Read More » -
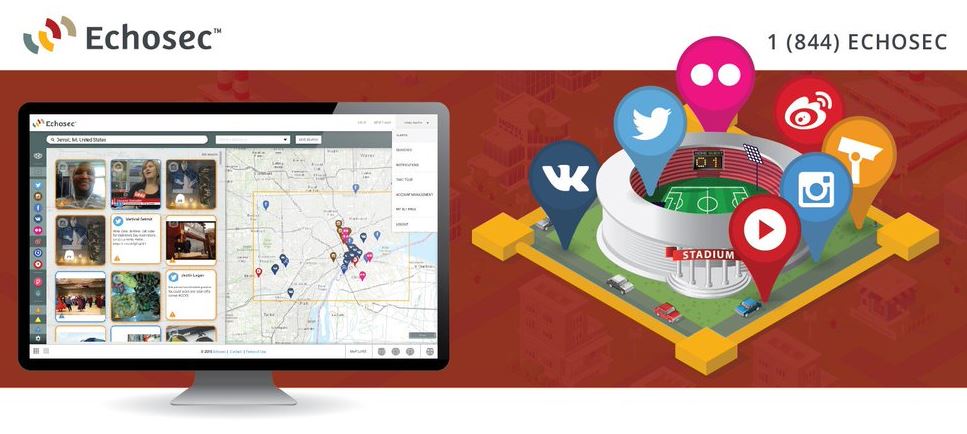
Introducing Echosec | Retrieve Anyone Location Who Posted Anything On Social Media
Retrieve Social Media Postings Locations That Were Made As Recently As a Minute or two ago One of the most…
Read More » -

Download Ethical Password Hacking & Protecting Course
Ethical Password Hacking & Protecting In this course you will learn Hacking Passwords and how really is it possible to…
Read More » -

Using Google Hacking
Using Search Engines One of the first step in the process of foot-printing tends to be using a search engine.…
Read More » -
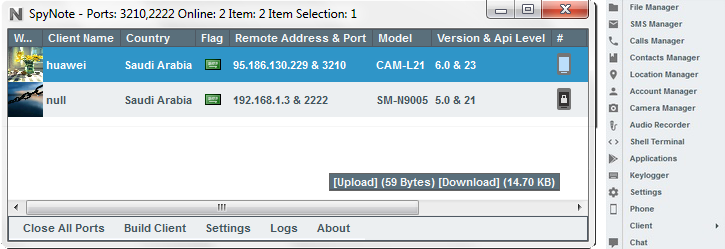
SpyNote Android Trojan Builder Leaked
SpyNote is a Android (APK) which basically which facilitates remote spying. The builder, which creates new versions of the malware,…
Read More »