IT Security
-
Understanding Hashing
Understanding Hashing Simply yet, hashing can be considered a type of one-way encryption. Most accurately, it is a process that…
Read More » -
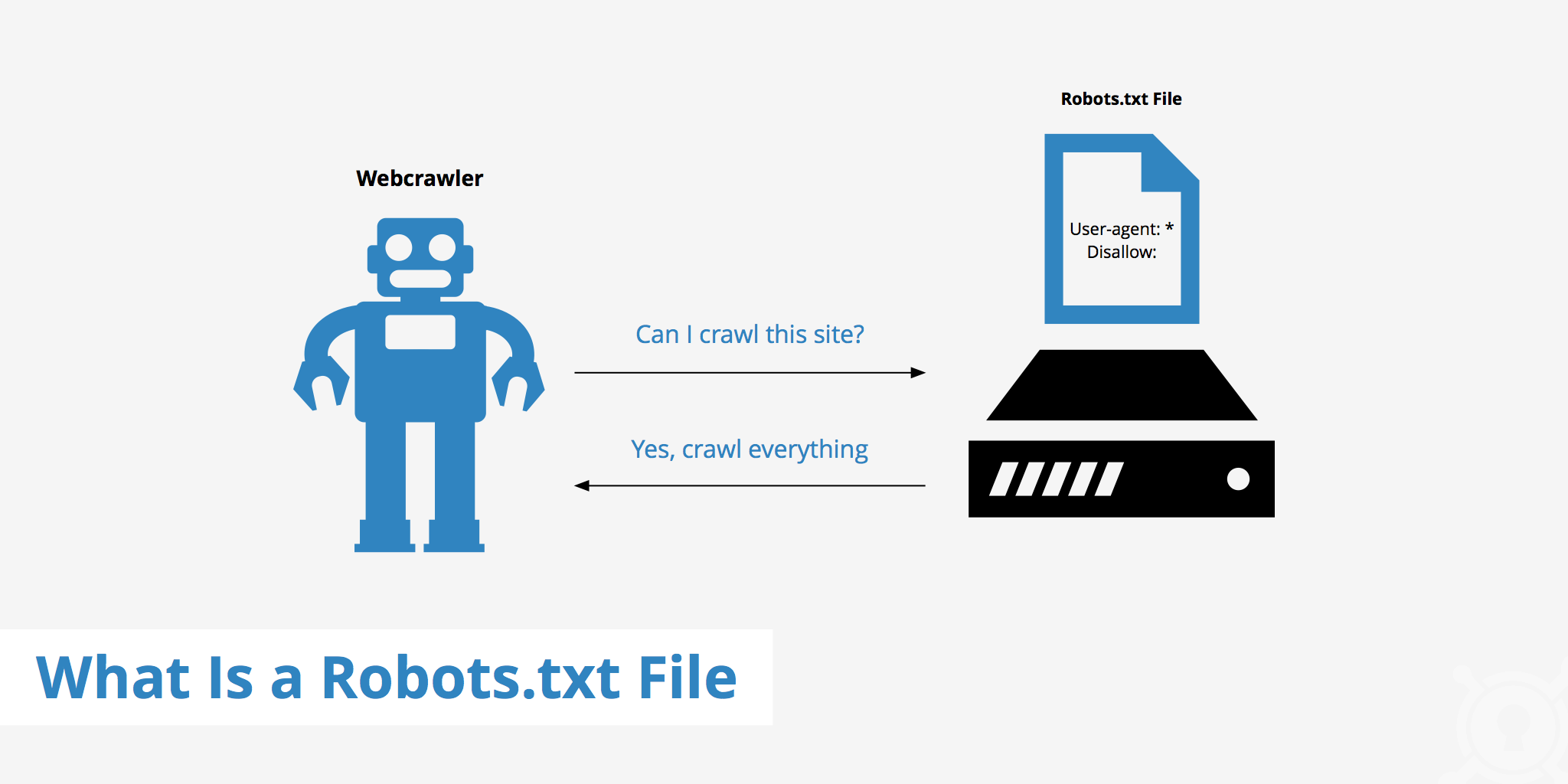
The Robots.txt File
The Robots.txt File One way to begin understanding what’s running on a web server is to view the server’s robots.txt…
Read More » -

JTR: KING OF THE PASSWORD CRACKERS
JTR: KING OF THE PASSWORD CRACKERS: It is hard to imagine discussing a topic like the basics of hacking without…
Read More » -

Password Cracking Techniques
Password-Cracking Techniques Popular culture would have us believe that cracking password is a simple as running some software and tapping…
Read More » -

Cyber Security Enhancement Act of 2002 – CSEA
Cyber Security Enhancement Act of 2002 – CSEA Several years ago, Congress determined that the legal system still allowed for…
Read More » -

Hunting Cross-Site Scripting (XSS)
Hunting Cross-Site Scripting (XSS) If you are not familiar with XSS attacks, make sure you read the OWASP article “Cross…
Read More » -

Social Engineering: The Art of Hacking Humans
What is Social Engineering? Social Engineering is a term that is widely used but poorly understood. It’s generally defined as…
Read More » -

A Complete Guide To WHOis, How To Find Domain Details
WHOis.net And Who.is And Whois in Linux Terminal A very simple but effective means for collecting additional information about our…
Read More » -
HTTRACK: WEBSITE COPIER
HTTRACK: WEBSITE COPIER Typically, we begin Step 1 by closely reviewing target’s website. In some cases, it may be helpful…
Read More » -

Wireless Technology in Business
In Every single minute counts in every company and wireless networks are the most powerful techniques for boosting the productivity…
Read More »