IT Security
-

VPNs and VPN Concentrators
VPNs and VPN Concentrators: A virtual private network (VPN) is a private network connection that occurs through a public networks.…
Read More » -

SQL: Bypassing Authentication
We can now construct a valid SQL statement that will execute gracefully and retrieve information that we have no rights…
Read More » -

SQL INJECTION ATTACKS: Finding the Vulnerability
SQL Injection Attacks: Now that we have the basics of SQL injection down, let’s use our DVWA environment to try…
Read More » -
The SQL Interpreter
SQL Interpreter: One of the main aspects of this vulnerability that you must understand is that it leverages an SQL…
Read More » -

SQL for Hackers: Learn How Useful SQL
SQL for Hackers: Learn How Useful SQL : As an attacker, it is critical to gain an understanding on how…
Read More » -
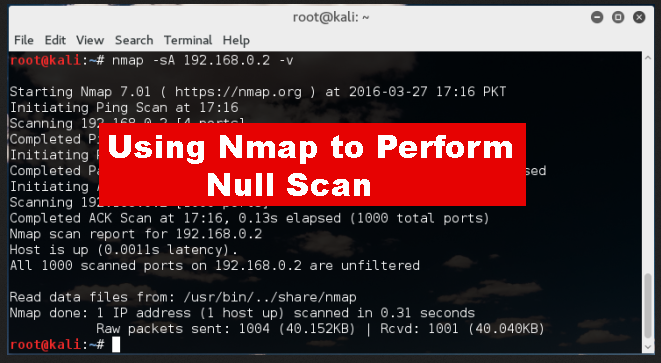
USING NMAP TO PERFORM NULL SCANS
USING NMAP TO PERFORM NULL SCANS: Null scans, Xmas tree scans, are probes made with packets that violate traditional TCP…
Read More » -

NMAP SCRIPTING ENGINE: FROM CATERPILLAR TO BUTTERFLY
THE NMAP SCRIPTING ENGINE: FROM CATERPILLAR TO BUTTERFLY: Make no mistake. Nmap is an awesome tool. It is mature, robust,…
Read More » -

PORT SCANNING WRAP UP
Port Scanning Wrap Up: Now that we have covered the basics of port scanning, there are a few additional switches…
Read More » -
NIKTO: INTERROGATING WEB SERVERS
NIKTO: INTERROGATING WEB SERVERS: After running a port scan and discovering a service running on port 80 on port 443,…
Read More » -
USING NMAP TO PERFORM AN SYN SCAN
USING NMAP TO PERFORM AN SYN SCAN: The SYN Scan is arguably the most popular Nmap port scan. There are…
Read More »