IT Security
-

Google Android OS – Security
Google Android OS: First, let’s look at the market leader, Android, in our exploration of mobile operating systems. Android took…
Read More » -

Mobile Security Models and Architectures
Mobile OS Models and Architecture: The rapid adoption of the mobile device in the workplace has had two obvious consequences:…
Read More » -
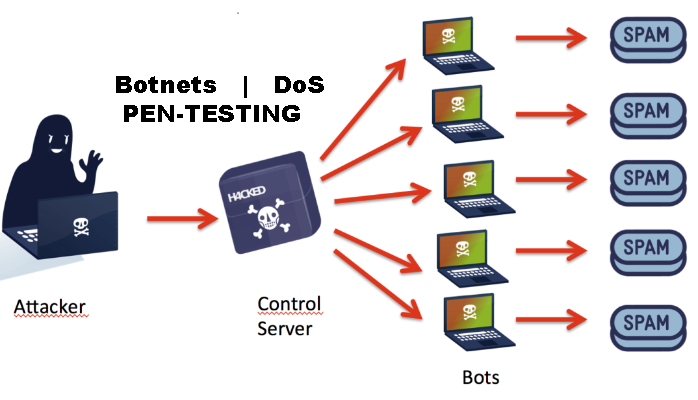
DoS | Botnet Specific Defensive Strategies
DoS | Botnet Specific Defensive Strategies: Let’s look at some DoS defensive strategies:- Disabling Unnecessary Services: You can help protect…
Read More » -

SSL and TLS
SSL and TLS: Secure Sockets Layer (SSL) is used to establish a secure communication connection between two TCP-based machines. This…
Read More » -
Understanding Cryptography Standards and Protocols
Understanding Cryptography Standards and Protocols: Numerous standards are available to establish secure service. Some of the standard that will be…
Read More » -

Phishing, Spear Phishing, and Vishing
Phishing, Spear Phishing, and Vishing: Phishing is a form of social engineering in which you ask someone for a piece…
Read More » -

Spoofing Attacks – Understanding Various Types of Attacks
Spoofing Attacks: A spoofing attack is an attempt by someone or something to masquerade as someone else. This type of…
Read More » -
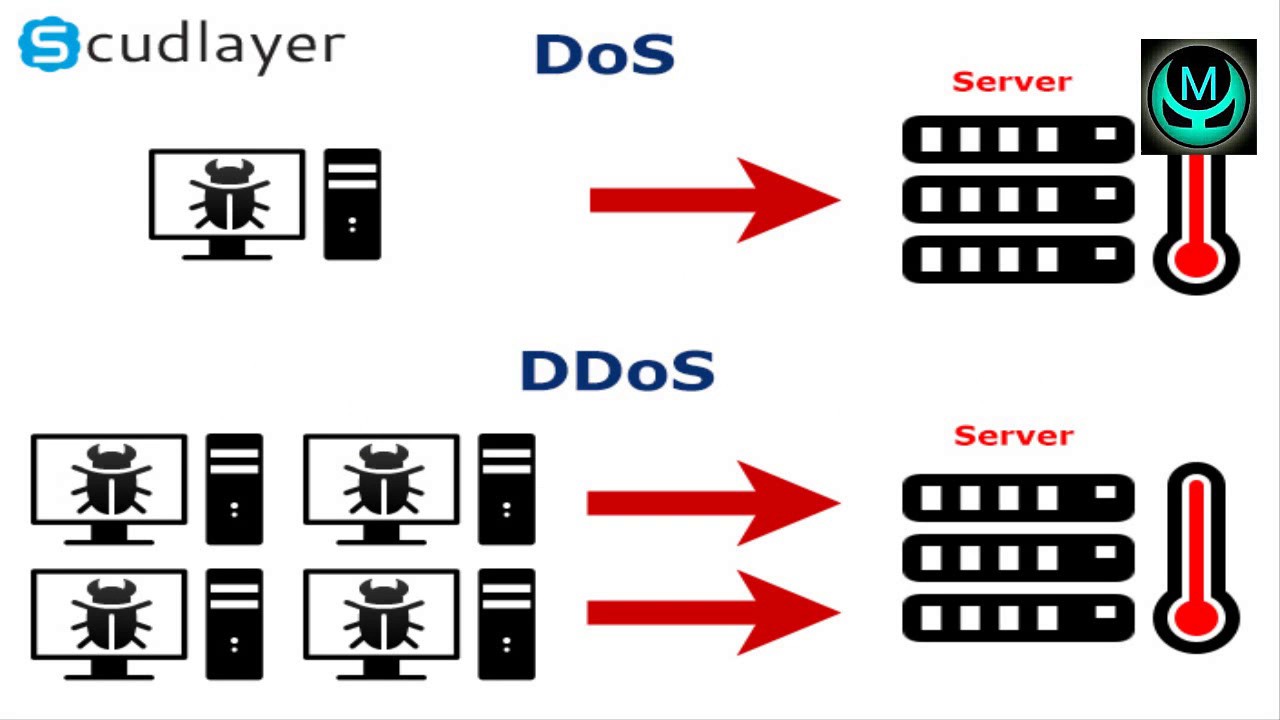
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks: Denial-of-service (DoS) attacks prevent access to resources by users authorized to use those resources.…
Read More » -

Top 10 Mobile Devices Security
Mobile Device Security: Mobile device, such as laptops, tablet computers, and Smartphones, provide security challenges above those of desktops workstations,…
Read More » -
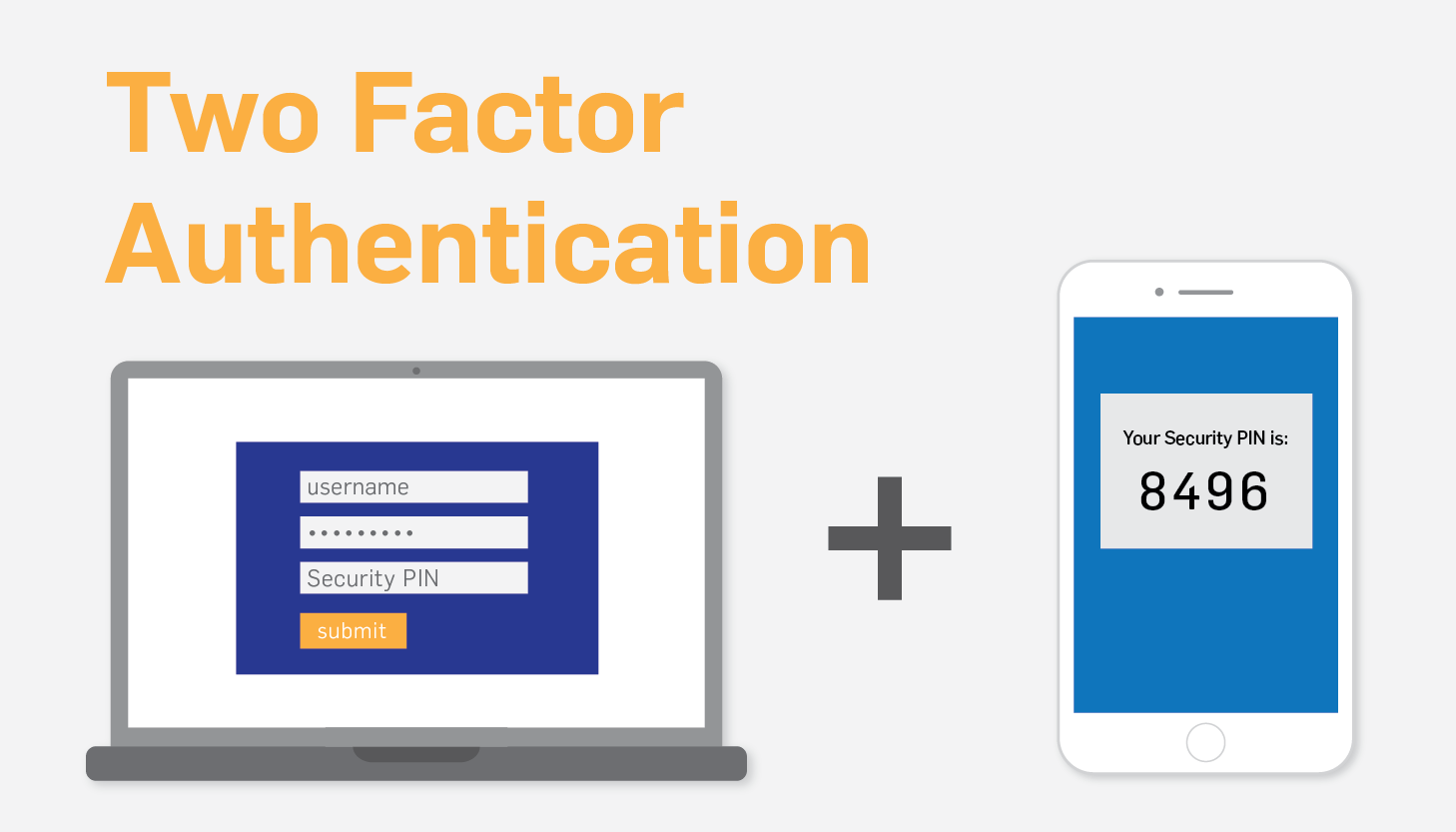
Authentication (Single Factor) and Authorization
Authentication (Single Factor) and Authorization: The most basic form of authentication is known as single-factor authentication (SFA), because only one…
Read More »