IT Security
-

Ways to Locate Wireless Networks
Ways to Locate Wireless Networks: In order to attack, you must first find a target, and though site surveys can…
Read More » -
USB Password Theft
USB Password Theft: In contrast to manual methods, there is some automated mechanism for obtaining passwords, such as via USB…
Read More » -
Performing a Password Crack – Insecure Logon Systems
Insecure Logon Systems: Many web applications require some sort of authentication or login process prior to their use. Because of…
Read More » -

Cracking WPA with Reaver and Wash
Cracking WPA: To crack WPA you must use a different approach than you would with WEP. Fortunately, one of the…
Read More » -

Cracking WEP with Kali Linux
Cracking WEP with Kali Linux: In this exercise you will use Kali Linux 2.0 to break WEP. To perform this…
Read More » -
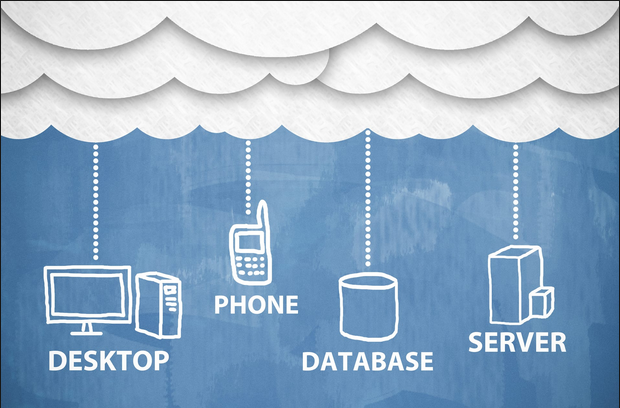
Types of Cloud Solutions
Types of Cloud Solutions: Calling the Cloud “the cloud” simply isn’t accurate because it doesn’t fully describe the scope of…
Read More » -

What is the Cloud Technologies and Security
What is the cloud: While cloud computing is new term, it is not a new concept and is actually a…
Read More » -
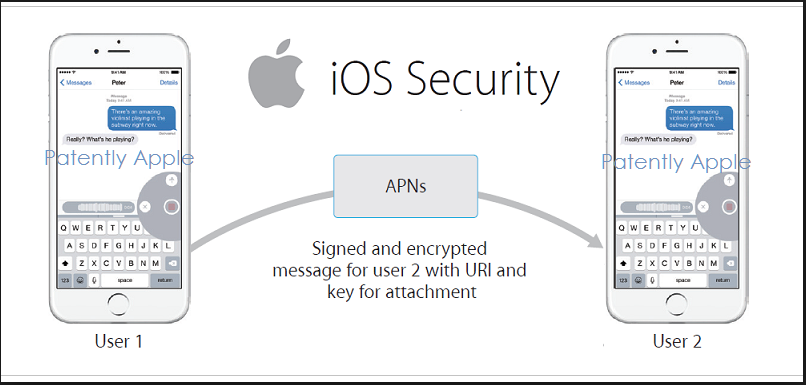
Apple iOS – Security
Apple iOS: The second most popular mobile operating system in the market is Apple’s iOS, which is present on multiple…
Read More » -

Design of Android – Security
Design of Android: Android, under the hood, is a series of components working together to make the system work. Each…
Read More »
