IT Security
-
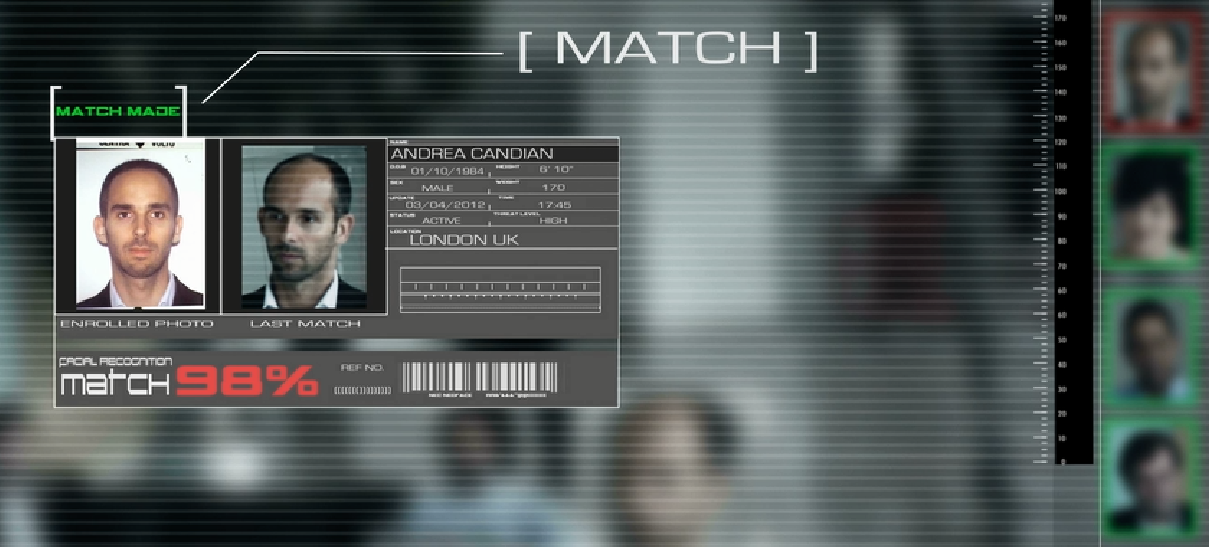
Facial Recognition – What You Are About to See Will Shock You
The Human face plays extremely important rule in our society interactions, which helps conveying the people’s identity. Using the Human…
Read More » -

PERSONNEL SECURITY
Users can pose the biggest security risk to an organization. Background checks should be performed, contractors who needs to be…
Read More » -

YouTube Launches New Tool For Finding and Removing Unauthorized Re-Uploads
Re-uploading videos on YouTube is a favorite scammy channel that gets profit from other people’s hard work. The Copyright owners…
Read More » -
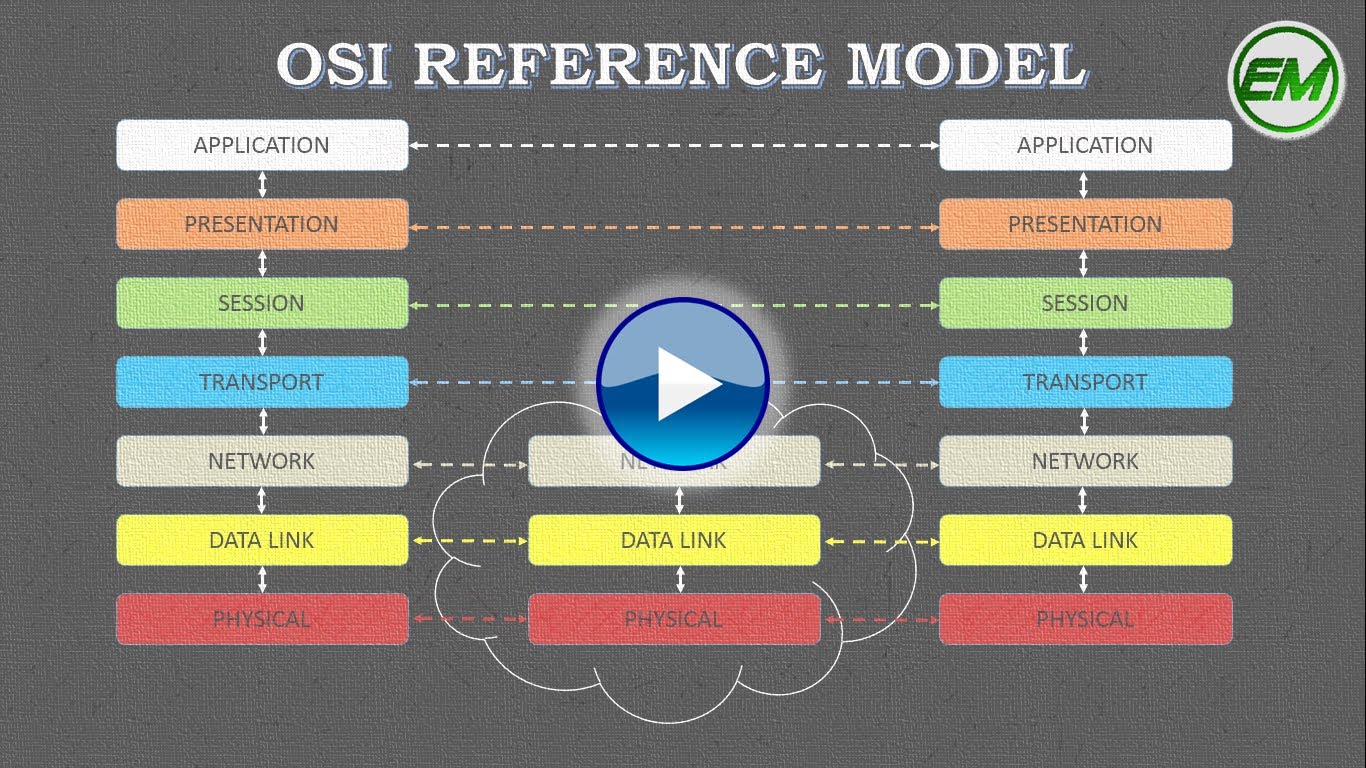
THE OSI MODEL
The OSI (Open System Interconnection) reference model is a layered network model. The model is of course abstract; we do…
Read More » -
SYSTEM VULNERABILITIES, THREATS, AND COUNTERMEASURES
System threats, vulnerabilities, and countermeasures describe security architecture and design vulnerabilities, as well as the corresponding exploits that may compromise…
Read More » -

Information Security Governance
Information security governance is the information security in the organizational level, which includes senior management, policies, processes, and staffing. It…
Read More » -

Legal and Regulatory Issues
Though general understanding of the major legal systems and their types of law is really essential, it is critical that…
Read More » -

Types of Attackers
Controlling access is not limited to the control of authorized users; it also includes preventing unauthorized access. Information systems may…
Read More » -

Protocol Analyzers
The terms protocol analyzing and packet sniffing are interchangeable. They refer to the process of monitoring the data that is…
Read More » -

AT&T Collaborates on NSA Spying Through a Web of Secretive Building in the US
A new report from The Intercept sheds light on the NSA’s close relationship with communications provider AT&T. The Intercept has…
Read More »