Black Hat
-
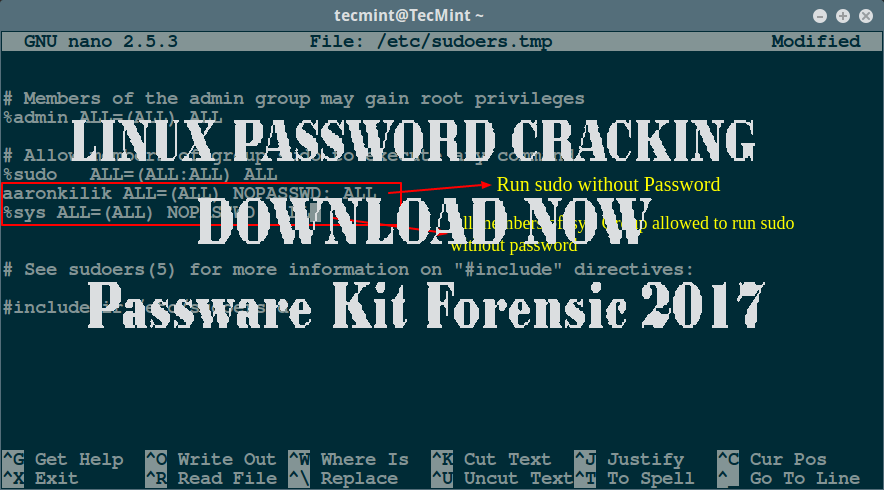
LINUX PASSWORD CRACKING AND A QUICK EXAMPLE OF PRIVALEGE ESCALATION
LINUX PASSWORD CRACKING AND A QUICK EXAMPLE OF PRIVALEGE ESCALATION: The process of cracking Linux and OS X passwords is…
Read More » -

GOOGLE DIRECTIVES: PRACTICING YOUR GOOLGE-FU
Luckily for us, Google provides “directives” that are easy to user and help us get the most out of every…
Read More » -
How to Delete WhatsApp Messages Even After Days Not Only after 7 Minutes – WhatsApp Bug
Delete WhatsApp messages from Everyone Even After Few Months Or Hrs Or Year: Recently, WhatsApp introduced the very new Features…
Read More » -
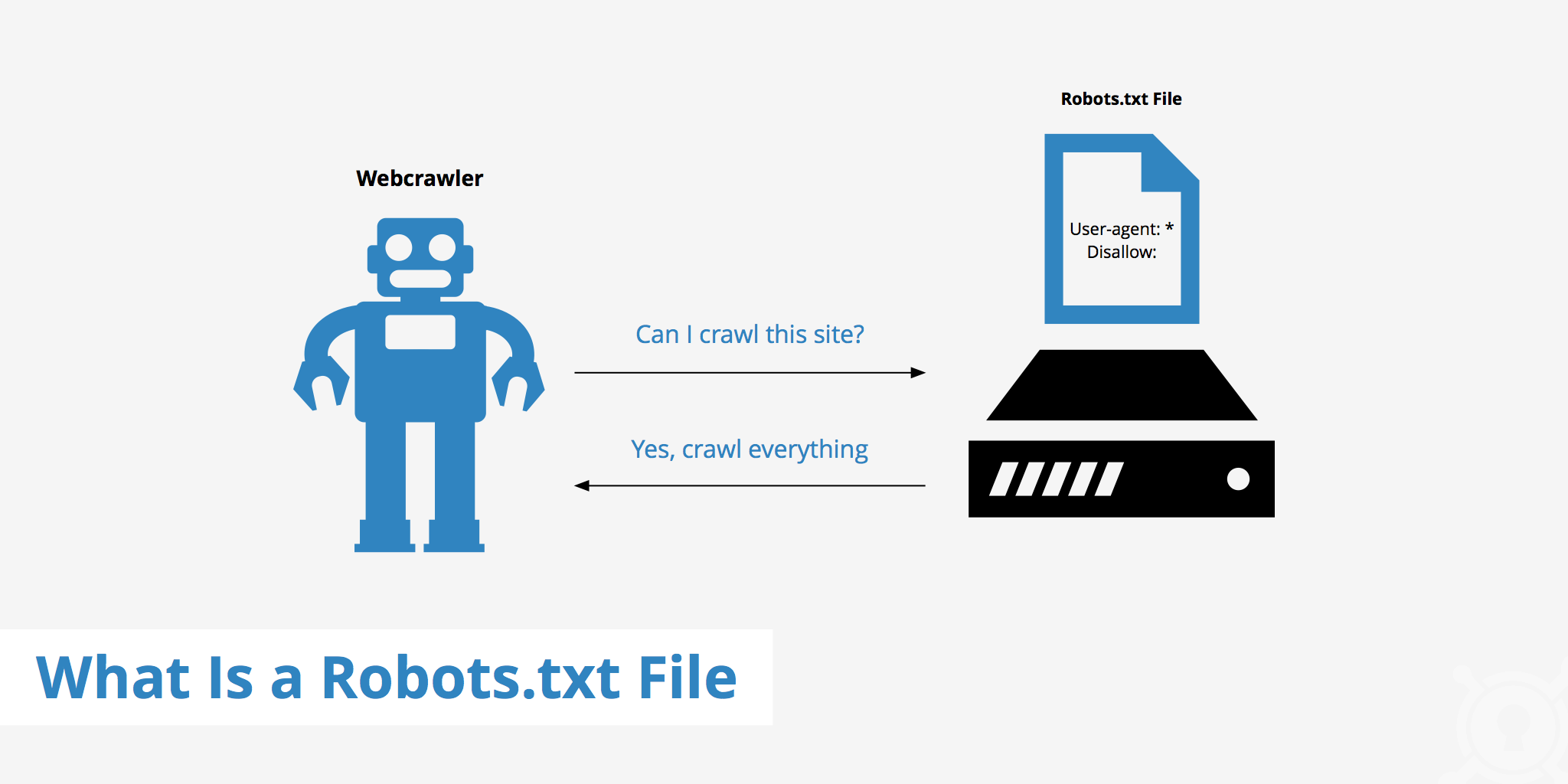
The Robots.txt File
The Robots.txt File One way to begin understanding what’s running on a web server is to view the server’s robots.txt…
Read More » -

JTR: KING OF THE PASSWORD CRACKERS
JTR: KING OF THE PASSWORD CRACKERS: It is hard to imagine discussing a topic like the basics of hacking without…
Read More » -

Password Cracking Techniques
Password-Cracking Techniques Popular culture would have us believe that cracking password is a simple as running some software and tapping…
Read More » -

Hunting Cross-Site Scripting (XSS)
Hunting Cross-Site Scripting (XSS) If you are not familiar with XSS attacks, make sure you read the OWASP article “Cross…
Read More » -
HTTRACK: WEBSITE COPIER
HTTRACK: WEBSITE COPIER Typically, we begin Step 1 by closely reviewing target’s website. In some cases, it may be helpful…
Read More » -
Locating Database on the Network
A tool that is effective at locating rogue or unknown database installation in SQL Ping 3.0, as described on the…
Read More » -

Introducing SQL Injection, SQL Attacks in Action And Results of SQL Injection
Introducing SQL Injection, SQL Attacks in Action And Results of SQL Injection The acronym SQL(pronounced sequel) stands for Structured Query…
Read More »