Black Hat
-

Operating System Command Injection Vulnerabilities
O/S Command Injection Vulnerabilities: Another attack vector that is part of injection is operating system command injection. This occurs when…
Read More » -

EXTRACTING INFORMATION FROM E-MAIL SERVERS
E-Mail Servers: E-mail servers can provide a wealth of information for hackers and penetration testers. In many ways, e-mail is…
Read More » -

Using a Sniffer – Sniffer Tools
Using a Sniffer: We touched on some of the basics of using a sniffer in the previous section, but now…
Read More » -

Planting a Backdoor – Using Netcat
Planting a Backdoor: There are many ways to plant a backdoor on a system, but let’s look at one provided…
Read More » -

DNS Spoofing – Performing DNS Spoofing
DNS Spoofing: DNS is an important service for just about any network today. Some networks, such as those that use…
Read More » -

Ways to Locate Wireless Networks
Ways to Locate Wireless Networks: In order to attack, you must first find a target, and though site surveys can…
Read More » -
USB Password Theft
USB Password Theft: In contrast to manual methods, there is some automated mechanism for obtaining passwords, such as via USB…
Read More » -
Performing a Password Crack – Insecure Logon Systems
Insecure Logon Systems: Many web applications require some sort of authentication or login process prior to their use. Because of…
Read More » -
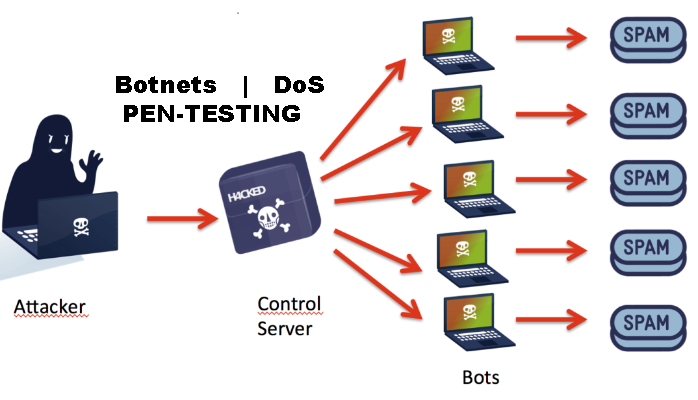
DoS | Botnet Specific Defensive Strategies
DoS | Botnet Specific Defensive Strategies: Let’s look at some DoS defensive strategies:- Disabling Unnecessary Services: You can help protect…
Read More » -
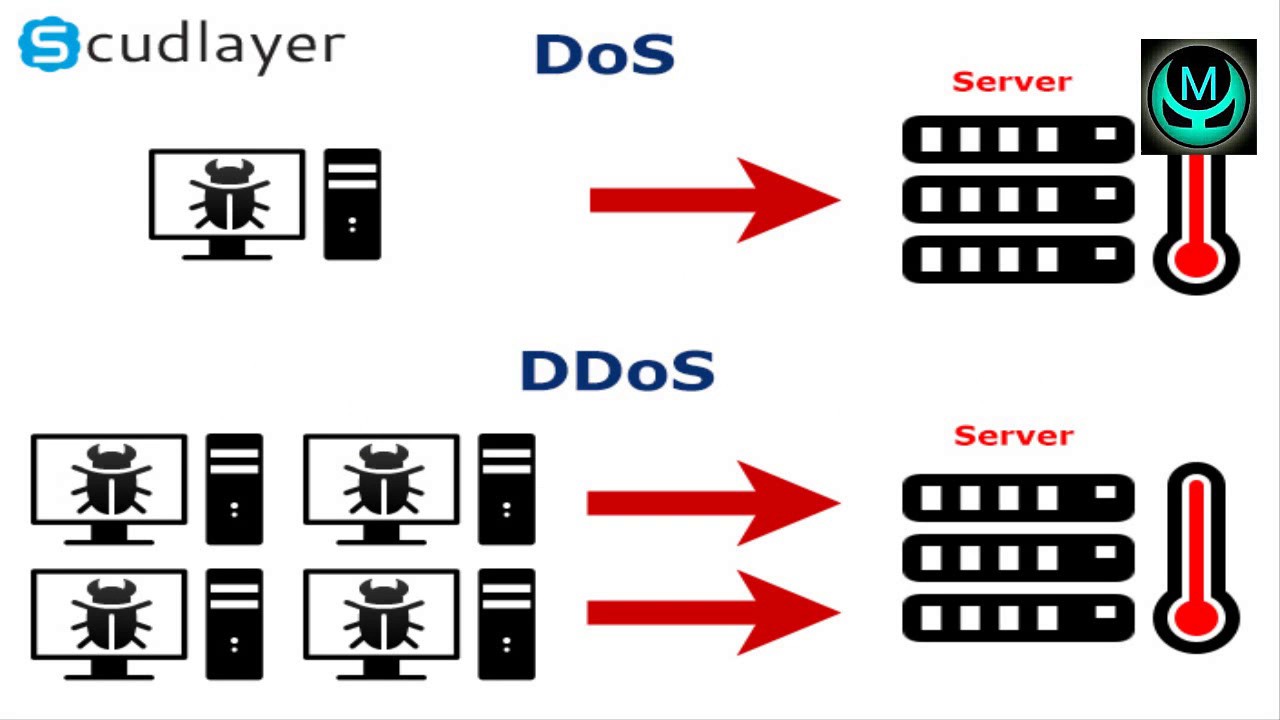
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks
Identifying Denial-of-Service and Distributed Denial-of-Service Attacks: Denial-of-service (DoS) attacks prevent access to resources by users authorized to use those resources.…
Read More »