Bykea Had Publicly Exposed 400+ Million Users Data Including [CNIC, Address, License] ETC
Rafay Baloch Pakistan’s Top Cyber Security Expert Posted an Update Regarding a Recent Data Breach of a Well Known Multi Million Dollar Company ‘BYKEA‘ on His Wall Stated The Following:
As per a report by Safety Detectives, Bykea بائیکیا had publicly ‘exposed 400 million files of Bykea Customer Personal data, Bykea partners (Drivers’) personal data’ and unencrypted employee login through a security misconfiguration.
The vulnerability was reported on 24th November and was fixed within 24 hours. However, Bykea decided to sweep it under the carpet and decided not to make any information public about the data breach.
Every now and then, Private companies hosting citizens data get breached and such issues are privately fixed and it’s shameful that details about these issues are not made public.
Also Read: Pakistan Citizens Data is No More Secured
If a company hosting citizen data, to maintain trust they should be transparent about any data breaches otherwise users should not to trust them with their personal data and boycott use of such applications.
It is pertinent to mention here that Bykea did suffer another breach in Sep 2020 where-by attackers reportedly wiped out the database, Bykea should issue clarification if the current exposure is anyway related to the Sep 2020 breach.
It is also worth questioning, if a small company size of Bykea would even host 400 million records given the fact that total population of Pakistan is roughly equivalent to 217 million
Also Read: Multimillion-dollar Pakistani delivery company leaks 400+ million files
Comments on This Data Breach From Pakistanis:
- Talha Qamar: If these companies are careless what you can expect from gov dept
- Muhammad Usama Rehmani: meaning anyone with a little bit of knowledge about the Shodan search engine could have accessed the database without needing to put any security authentication
Replied By Rafay: There are many pertinent questions which need to be answered, was the publicly available dump accessed by other entities, if yes how many times?, was entire data dumped?, were records held unencrypted?, were leaked employee creds used to obtain access? etc
February 3rd; Rafay Baloch Statement:

Bykea has released a press release issuing clarification about recent report on Safety Detectives post about leakage of 400+ million files.
In a press release, Bykea has admitted that they were storing drivers personal data unencrypted prior to this report, which now as per their claim has been encrypted.
On the flipside, the article by “Safety Detectives” is quite misleading in number of ways, by use smart rhetoric a perception was being created that a data leak/breach has occurred where-as in reality, SafetyDetectives reported a vulnerability which could have led to data exposure. There is a difference between something that is likely to happen vs something that has already happened. Closer inspection of the article would reveal use of keywords like “What was leaked?”, “Number of records leaked”, “Data breach impact” etc which are not directly related to the content.
Another point worth mentioning is that the figure quoted by “Safety Detectives” was also deceptive. While unencrypted personal data was exposed through the vulnerability, however their statement gives reader an impression that the all 400 million+ records exposed contained personal data which is almost twice to the total size population of Pakistan.
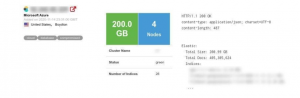
To quote them. “Bykea had exposed all its production server information and allowed access to over 200GB of data containing more than 400 million records showing people’s full names, locations, and other personal information”. Bykea has responded to this by claiming that majority of the 400 million records were GPS coordinates.
Finally, Safety Detectives article talks about “Preventing Data Exposure” which only gives generic recommendations to users and are not directly related to this vulnerability which falls under category of security misconfiguration. None of the recommended steps will fix Security misconfiguration vulnerabilities.
Also Read: Bykea admits vulnerability in its database but denies any breach
What Was Leaked?
Bykea customer’s PII:
- Full names
- Phone numbers
- Email addresses
Bykea partners’ (drivers’) PII:
- Full names
- Phone numbers
- Address
- CNIC (Computerised National Identity Card)
- Driver license numbers, issuing city and expiry dates
- Body temperature
Other information was also left unsecured, such as:
- Internal API logs
- Collection and delivery location information
- User token ID with cookie details and session logs
- Specific GPS coordinates
- Vehicle information including model and number plate
- Driver license expiry information
- Miscellaneous user device information
- Encrypted IMEI numbers
| Number of records leaked: | 400+ million |
| Number of affected users: | Unknown |
| Size of data breach: | 200+ gigabytes |
| Server location: | Boydton, United States |
| Company location: | Karachi, Pakistan |




One Comment