Apple iOS – Security
Apple iOS: The second most popular mobile operating system in the market is Apple’s iOS, which is present on multiple devices including the iPod, iPad, and iPhone.
Much as Android is based on the linux Kernel, iOS is a slimmed-down version of OS X for the Mac. However, while it is based on OS X, which is based on FreeBSD, it is not fully Unix compatible.
Unlike Android, which covers all five core components of system design, iOS covers only four. Specifically, it addresses these areas:
Traditional Access Control iOS provides traditional access control security options, including password configuration options as well as account lockout options.
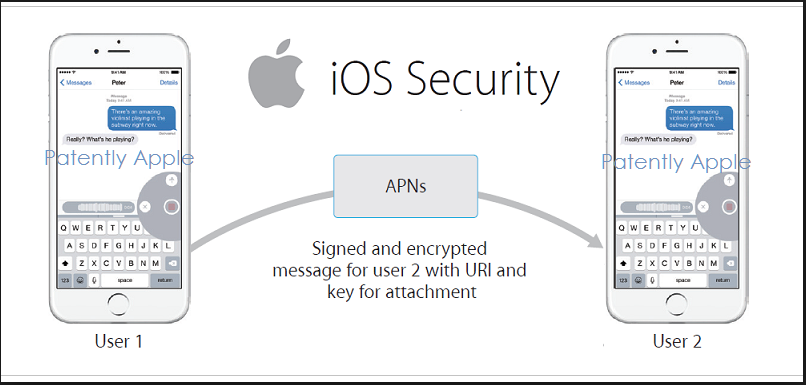
Application Provenance Just as Android items that are in the Google Play store have been verified and therefore trusted, in iOS it’s the same type of deal with apps being created by Apple-approved developers, who have the ability to sign their app before placing it in the store.
Encryption iOS uses hardware-accelerated AES-256 encryption to encrypt all data stored on the device as well as additional encryption for email and other services.
Isolation The iOS operating system isolates each app from every other app on the system, and apps aren’t allowed to view or modify each other’s data, logic, and the like.
There is something to pay attention to and expand upon in this list, something that is more than it appears, and that is the application provenance issue.
Both Android and iOS use this to ensure that apps that are installed by the user come from legitimate sources, meaning approved developers.
However, users of Apple devices can’t install non-Apple approved applications on their phone as Android users can.
But with this in mind, you may have seen an iPhone or two running an app or something else that didn’t come from the App Store.
SO how does this occurs?
Through a process known as jailbreaking. So what is jailbreaking, and how does it works? Let’s talk about this a bit.
First of all, you need to understand that many manufactures of Smartphones, tablets, games console, and other systems include digital rights management (DRM) in their products.
DRM exists to control the types of software you can run on your devices as well as get around the restrictions imposed by DRM and let you run whatever you want to run and do whatever you want to do on the device.
From a technical standpoint, jailbreaking is simply applying a set of kernel-level patches to a system that allows the owner of the device to run unsigned applications.
This process also grants root access to the device and removes the restrictions associated with having non-root access.
One drawback of this process is a little thing called voiding your warranty. Another drawback is that you are effectively opening the device up with so much access that anything can run without restrictions, including malware.
If you have any question regarding Apple iOS you may ask in the comment section below.




i read the full article this is great info about tech
Thank you brother.