
Burp Suite
Burp Suite: For our purposes, we will use Burp Suite Intercept (or just Burp for short) as our proxy as it is widely viewed as one of the most feature-rich web hacking platform available.
We will be using many tools in Burp Suite throughout the duration of our hacking approach. Burp Suite is available in BackTrack, but for more information or to download Burp Suite as a stand-alone file, check out www.portswigger.net.
Burp Suite can be opened in BackTrack via Application >BackTrack > Vulnerability Assessment > Web Application Assessment > Web Application Proxies > Burpsuite as shown below.
Burp Suite may take a few seconds to load the first time, so be patient if you don’t see immediate action.
Depending on your version of BackTrack, you may also see a warning about the Java runtime environment (JRE). Click OK to continue and then accept the license agreement.
If you receive notifications that there are newer versions of Burp Suite available for download, feel free to install them.

CONFIGURING BURP PROXY
- Open Firefox (From the Application > Internet menu) then choose Edit > Preference
- Choose the Advanced menu at the top of the Firefox Preferences box
- Choose the Network tab and then click Settings
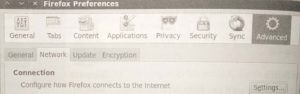
Configuring Firefox to use a proxy for Internet communications.
- Select the Manual Proxy Configuration radio button and enter 0.0.1 in the HTTP Proxy input box
- Enter 8080 in the Port input box
- Clear the No Proxy For input box, make sure the Connection Settings mirror, and click OK
- Close the Firefox Preferences window.

ALERT
While Burp Suite runs on 8080, other proxies may use a different port number. Be sure to use the correct port if you choose to use a different proxy. Also, we removed the entries in the “No Proxy For” input box because out target is on Localhost. When accessing a remote web application, you don’t need to edit the entries found in the “No Proxy For” textbox.



