LINUX PASSWORD CRACKING AND A QUICK EXAMPLE OF PRIVALEGE ESCALATION: The process of cracking Linux and OS X passwords is much the same as the method described above with a few slight modifications. Linux systems do not use an SAM file to store the password hashes. Rather the encrypted Linux password hashes are contained in a file called the “shadow” file which is located at /etc/shadow.
The bad news is that only privileged user can access the /etc/shadow file. If you have the appropriate the privilege level to view the /etc/shadow file, there is another method. Linux also makes use of a redacted password list located at /etc/passwd. This list is typically readable by all users and we can utilize a special function included with JtR to combine the /etc/shadow and /etc/password lists. The output of this process is a single list which includes the original hashes. This new list can then be fed into John and cracked like all of our previous examples.
In many respects, this is similar to how we had to use the “system” file with the SAM file to extract Windows password hashes. Unprivileged users can combine the /etc/shadow and /etc/passwd lists by utilizing the “unshadow” command. To combine the two lists, issue the following command in a terminal:
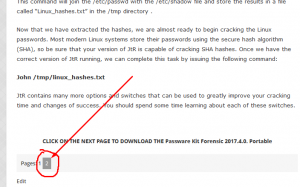
Unshadow /etc/passwd /etc/shadow > /tmp/linux_hashes.txt
This command will join the /etc/passwd with the /etc/shadow file and store the results in a file called “Linux_hashes.txt” in the /tmp directory .
Now that we have extracted the hashes, we are almost ready to begin cracking the Linux passwords. Most modern Linux systems store their passwords using the secure hash algorithm (SHA), so be sure that your version of JtR is capable of cracking SHA hashes. Once we have the correct version of JtR running, we can complete this task by issuing the following command:
John /tmp/linux_hashes.txt
JtR contains many more options and switches that can be used to greatly improve your cracking time and changes of success. You should spend some time learning about each of these switches.
CLICK ON THE NEXT PAGE TO DOWNLOAD THE Passware Kit Forensic 2017.4.0. Portable